This is a guest post by Sam Bocetta.
In the world of digital business, there’s no safety in being small when it comes to online threats.
In truth, small businesses are a common target of cybercrime with a single attack typically costing between $84,000 and $148,000. If you want to keep your customers’ data protected and avoid damage to your revenues and reputation, then you need to pay attention to IT security. A strong firewall is a good place to start.
A firewall can be either a physical hardware device or a software tool. Both types are responsible for checking incoming data traffic and determining whether to block or allow it through to its destination. Here’s why firewalls are essential to small business security.
Access Control
A firewall operates at the network layer and recognizes all incoming requests based on their internet protocol (IP) address. IP addresses are all unique and are assigned by your internet service provider (ISP).
When first setting up access controls with a firewall, you must decide whether you want to start with open access or closed one. With open access, all external IP addresses are allowed to send traffic to your network except for ones that you explicitly block. Closed access is the opposite, with all traffic blocked except for IP addresses that you mark as allowed.
For a small business, you obviously want to allow open access to your public-facing website, so that outside visitors can browse to it. However, the back-end servers managing the site and related applications should have stricter controls. In most cases, their firewall policies should be set up with closed access first.
Cloud Implications
In the early days of the internet, companies hosted websites and applications on servers that were housed in their own physical office or location. Over time, the trend shifted to putting resources into shared data centers, which has evolved into the cloud computing movement of today.
For a small business, hosting data, applications, and services in the cloud often represents a wise financial decision. Maintaining physical servers in an office environment or small data center requires a great deal of energy and repair costs. With the cloud, you will only pay for the services you use on a monthly basis.
But trusting IT resources in the cloud comes with a certain level of risk. You lose physical access to your data and become part of a shared network environment. As a result, maintaining a strict firewall policy is critical for cloud customers. Otherwise, you could risk leaving your data exposed and vulnerable to hacks.
Securing Databases
Websites and mobile applications all require some sort of back-end database system to run. Otherwise, the front-end interface will have nothing to interact with or display. For example, if your small business website has a mailing list sign-up form, then each online submission is sent from the user’s browser to the site’s database.
So how do you go about keeping back-end databases safe and secure? A firewall is one of the most important tools to use.
Your web server will need to communicate with the database in order to add new records or retrieve old ones, but that does not mean external users or systems should have direct access to that layer of information. Otherwise, you are at risk of suffering from a dangerous SQL injection attack, where a hacker will manipulate a website to expose back-end data.
You should configure your firewall so that only internal IP addresses from approved application servers can connect to the ports on the database server. All other connections should be blocked entirely.
This setup will provide a significant level of security since even if a database password is lost or stolen, outside individuals will not be able to access the back-end server to use it.
Virus Protection
Modern firewalls can do more than just filter network traffic based on IP addresses. One of their other primary advantages is the ability to detect and block malicious network requests. The success of this feature all depends on the firewall tool and provider that you choose.
No matter what, the most important thing to remember is to keep your firewall updated with the latest anti-virus definition files. Most firewall tools will check for these on a daily basis and install them as quickly as possible to protect against new threats. Doing this ensures that the firewall knows which ranges of IP addresses to flag and block as malicious.
The primary focus for firewalls is typically on the HyperText Transfer Protocol (HTTP), which is what browsers like Google Chrome and Mozilla Firefox use to load web content.
However, today’s strongest firewalls also offer protection through the Simple Mail Transfer Protocol (SMTP). This means that you can add firewall security to your email server and let it check for dangerous viruses and attachments that could be spread to your business through incoming messages.
Protecting Local Networks
Protecting back-end servers is pivotal to ensuring the security of your small business data, but if you leave your local ethernet and wireless networks exposed then you are creating just as much risk. Hackers are constantly looking for ways to infiltrate organizations through a single computer or device so that they can execute a wider attack from there.
Firewall restrictions should be applied at a global level, taking into account all users and hardware that need to connect to the local network at your place of business. Only the IT team should be allowed to make changes to this policy, and the list of blocked IP addresses should be reviewed on a regular basis.
In addition to IP address filtering, firewall tools will also give you the option to control which network ports are enabled or blocked for computers on your local network. HTTP communication occurs over port 80 (or port 443 for encrypted connections with HTTPS). Leaving all ports open on a workstation can result in the computer being hacked or infected with a virus.
If you plan to host guests or clients in your office location, you’ll likely want to provide them with wireless internet access. However, you should avoid granting them full access to your primary wi-fi network and instead set up a secondary guest network with restrictions that are controlled behind a firewall.
Verifying Remote Connections
Small businesses need to be flexible and dynamic in order to stay successful and grow larger. You can’t expect all of your company operations to occur within a single physical location or network. Chances are, you’ll have to travel for work or may want to hire remote or freelance employees.
But if your firewall is completely restricted to internal connections and traffic, then any attempt at working from a remote location will be blocked. To work around this, consider investing in a virtual private network (VPN) solution.
With a VPN, you set up a dedicated endpoint server in your company office or on your cloud platform that is responsible for handling and managing remote connections. Then, individual users and employees can connect to a personal VPN client, which will launch an encrypted session between their device and the VPN endpoint server.
A VPN tool functions like a secure tunnel, blocking all external threats and hackers from being able to decode the data being passed through your network. This means that you can safely work from anywhere in the world, even a public wi-fi network, and be confident that your data will be kept secure.
Another benefit of VPN solutions is that they will automatically assign localized IP addresses during a remote session. So once you connect to a VPN client, your true IP address will shift to an internal one, as opposed to the one assigned by your ISP. As a result, you should not need to make significant firewall configuration changes in order to add support for the VPN service.
Monitoring and Alerting
The most basic firewall systems function like traffic lights. Based on the policy you define, they either let network requests through to their destination or block them from passing into the local network. More modern solutions can offer advanced functionality, such as robust incident monitoring and alerting.
Think of these new firewall tools as high-tech traffic lights that monitor the flow of cars and track all nearby activities. Basically, they have a database of their own where they can store a history of network actions and use that for automatic analysis that requires minimal input from a human.
With a professional firewall solution, you can turn on a monitoring and alerting system that will record all incoming network activity and identify patterns that occur. Why is this helpful? Because the longer the firewall is in place and the more data it records, then the better the system gets at detecting and blocking threats.
As a small business owner, you surely don’t have enough time in the day to be constantly monitoring network logs. But with a good firewall tool, you can be alerted when something needs your attention, such as a sudden spike of traffic from a specific range of IP addresses.
From there, you can decide whether to block the requests entirely or throttle the performance so that the firewall only allows through a certain amount of traffic each minute. This way, your firewall becomes a smart street light that helps keep traffic flowing smoothly.
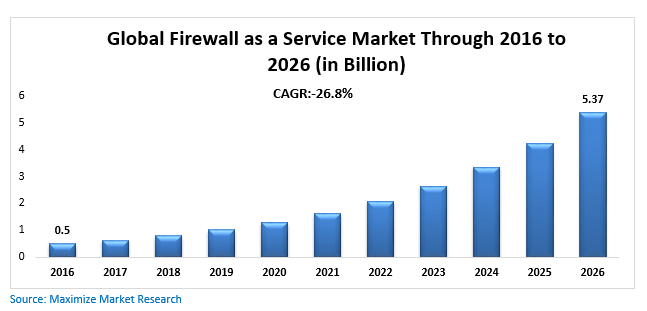
Firewall as a Service
Large companies typically have one or more physical hardware firewalls installed at different segments of their network. But since these devices are often costly, small businesses tend to invest in software-based solutions that offer similar functionality but come with slightly more risk. After all, any piece of software is vulnerable to hacking.
These days, you can now add firewall protection to your existing cloud environment through a concept known as firewall as a service (FWaaS). This means that you do not need to install a separate application on individual computers, servers, or mobile devices. Instead, all of that firewall configuration is handled in the cloud and deployed to every aspect of your hosted environment.
Investing in firewall as a service makes a lot of sense for any small businesses that expects to have employees accessing system resources or email from mobile devices such as smartphones and tablets. With a more traditional firewall solution, IT teams would need to manually configure each desktop or laptop computer, but would have little control over mobile devices. With firewall as a service, all traffic is treated the same in the cloud, regardless of device type.
Shifting your firewall solution to the cloud can be beneficial because of the flexibility and scalability it will provide. Traditional hardware and software firewalls have limits to how much network traffic they can monitor and filter in a given period of time.
But by integrating your security configuration with other cloud services, the firewall’s capacity will grow alongside your business. And best of all, firewall as a service will typically cost significantly less than other options.
The Bottom Line
If all this firewall talk seems impossibly complicated, well, maybe it is, but that’s no reason to stick your fingers in your ears and block it out. Remember the statistic from the beginning of this article? How each hack incident costs a small business anywhere from $84,000 to $148,000? That’s a sum of money that many companies can’t survive. They end up shutting down.
This way, firewall is paramount to ensuring the safety of your business operations. Are you taking proper care of your website and databases?